Junior Security Operations Analyst
This role involves overseeing and managing event logs and alerts to ensure the security of an organization's digital environment.
Responsibilities:
-
Monitor and Investigate Alerts: A significant part of the job involves keeping a constant watch on alerts, even around the clock in a 24x7 Security Operations Center (SOC). This means being vigilant for any signs of potential threats.
-
Configure and Manage Security Tools: Security tools such as Intrusion Detection Systems (IDS) need to be set up properly and maintained. These tools help identify potential breaches or malicious activities.
-
Develop and Implement Basic IDS Signatures: To improve the effectiveness of IDS, you might create specific "signatures" or patterns that the system can look for to spot known attack methods.
-
Participate in SOC Working Groups and Meetings: Collaboration is key. Being part of discussions and groups within the SOC helps ensure everyone is on the same page and can respond effectively.
-
Escalate Security Incidents: If a situation goes beyond the initial assessment, you'll escalate it to more experienced colleagues for further investigation.
Qualifications:
- 0-2 Years in Security Operations: This role is often an entry-level position, suitable for those just starting in the field.
- Basic Networking Knowledge: Understanding how data moves through networks (OSI model) is essential for detecting anomalies.
- Knowledge of Windows, Linux, Web Applications: Familiarity with different operating systems and common web technologies helps recognize abnormal behavior.
- Scripting/Programming Skills: While not always required, having skills in scripting or programming can be a plus, especially for tasks like automating certain processes.
Desired:
- CompTIA Security+: This is a well-regarded certification in the security field that covers foundational concepts.
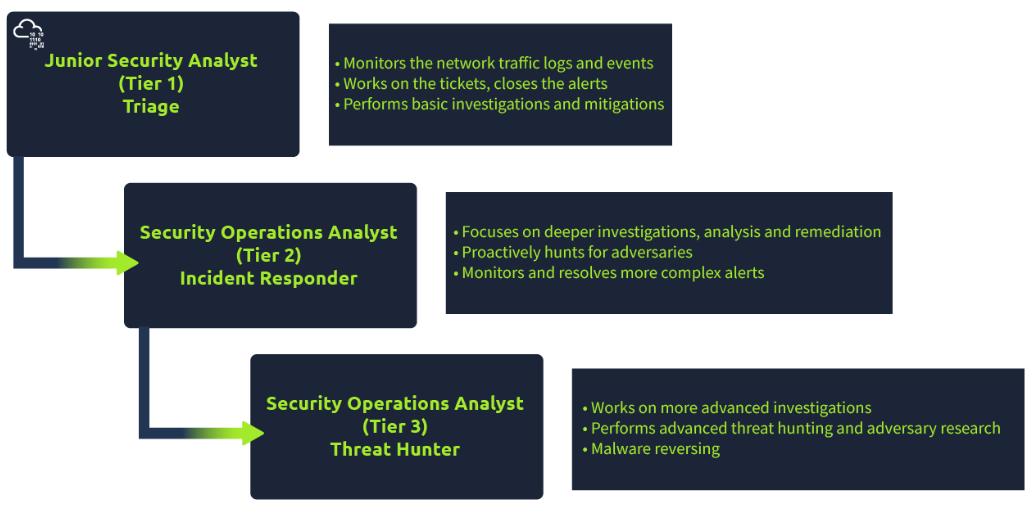
- Security Operation Center Three-Tier Model: Understanding the three-tier model (junior, mid-level, and senior analysts) helps you know where you fit and where you can progress.
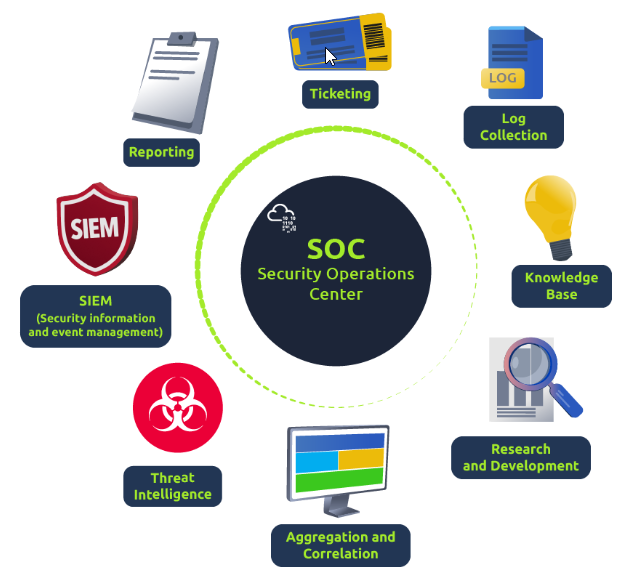
Core Functions of SOC:
-
Investigate, Monitor, Prevent, and Respond to Threats (24x7): The SOC's primary mission is to stay vigilant around the clock, analyzing incoming data for any signs of threats. This includes actively preventing breaches and quickly responding when they occur.
-
Protect Organizational Assets: This encompasses safeguarding everything valuable to the organization, from sensitive data and business systems to the company's reputation.
Preparation and Prevention:
-
Stay Informed: Being aware of current cyber threats is crucial. You can use platforms like Twitter and Feedly to stay up-to-date with the latest news and trends.
-
Security Roadmap: Developing a strategic plan helps your organization be ready for worst-case scenarios. This involves a combination of technologies, policies, and procedures to mitigate risks.
Prevention:
-
Gathering Intelligence Data: Understanding the latest threats, who the threat actors are, and their methods (TTPs) assists in building effective defenses.
-
Update Signatures and Patch Vulnerabilities: Keeping firewall signatures current and patching vulnerabilities prevents attackers from exploiting known weaknesses.
-
Application Whitelisting/Blacklisting: Managing lists of approved (whitelisted) and prohibited (blacklisted) applications, email addresses, and IPs help control potential threats.
Monitoring and Investigation:
-
Monitoring: This proactive approach involves using specialized tools like Security Information and Event Management (SIEM) systems and Endpoint Detection and Response(EDR) systems to monitor network activities for suspicious patterns.
-
Investigation: If an alert is triggered, it's important to understand the attack's methods and motives. Analyzing data logs and using open-source tools can help gain insights.
A Day in the Life of a Junior Security Analyst:
Before an Incident: Before any potential security incident occurs, your day starts by examining tickets and analyzing logs and alerts that have been generated.
Incident Response:
-
Duration: Incident response can vary widely, taking hours, days, or even weeks to fully address.
-
Key Questions: During an incident, you'll ask important questions: Was data taken? How much? Did the attacker move to other systems?
-
Stages: Incident response typically follows three main stages:
- Detection: Identifying that a breach or attack has occurred.
- Containment: Isolating affected systems to prevent further damage.
- Remediation: Fixing the vulnerabilities and restoring normal operations.